NASHUA, N.H. – Providing machines with human-like intelligence — only faster; cruise missiles that streak through the air at one mile per second; unmanned vehicles that require no human supervision; networked computers that are impervious to hackers; weapons that use laser light instead of bullets … these are only a portion of the military applications and enabling technologies that could make their mark the 2020s.
Here are some more: secure wireless communications able to control unmanned vehicles, military resupply, and battle management; rehearsing critical missions through virtual reality; a new generation of open-systems embedded computing; affordable satellites able to blanket the earth with communications and sensors; and the ability to navigate anywhere in the world without GPS signals.
These capabilities represent the top military applications and enabling technologies that will dominate the third decade of this century. Our list: artificial intelligence (AI) and quantum computing; hypersonic munitions; autonomous unmanned vehicles; cyber security and cyber warfare; directed-energy and laser weapons; 5G wireless communications; virtual and augmented reality in simulation, training, and mission rehearsal; SOSA and open-systems standards; New Space; and alternatives to GPS navigation.
AI and quantum computing
Artificial intelligence seeks to develop new kinds of computer hardware architectures, software operating systems, programming languages, and software programs for applications like machine autonomy, aids for human decision making, military maintenance, logistics and resupply, fast sensor and intelligence data processing, unmanned vehicles command and control, realistic simulation and training, and military planning and battle management.
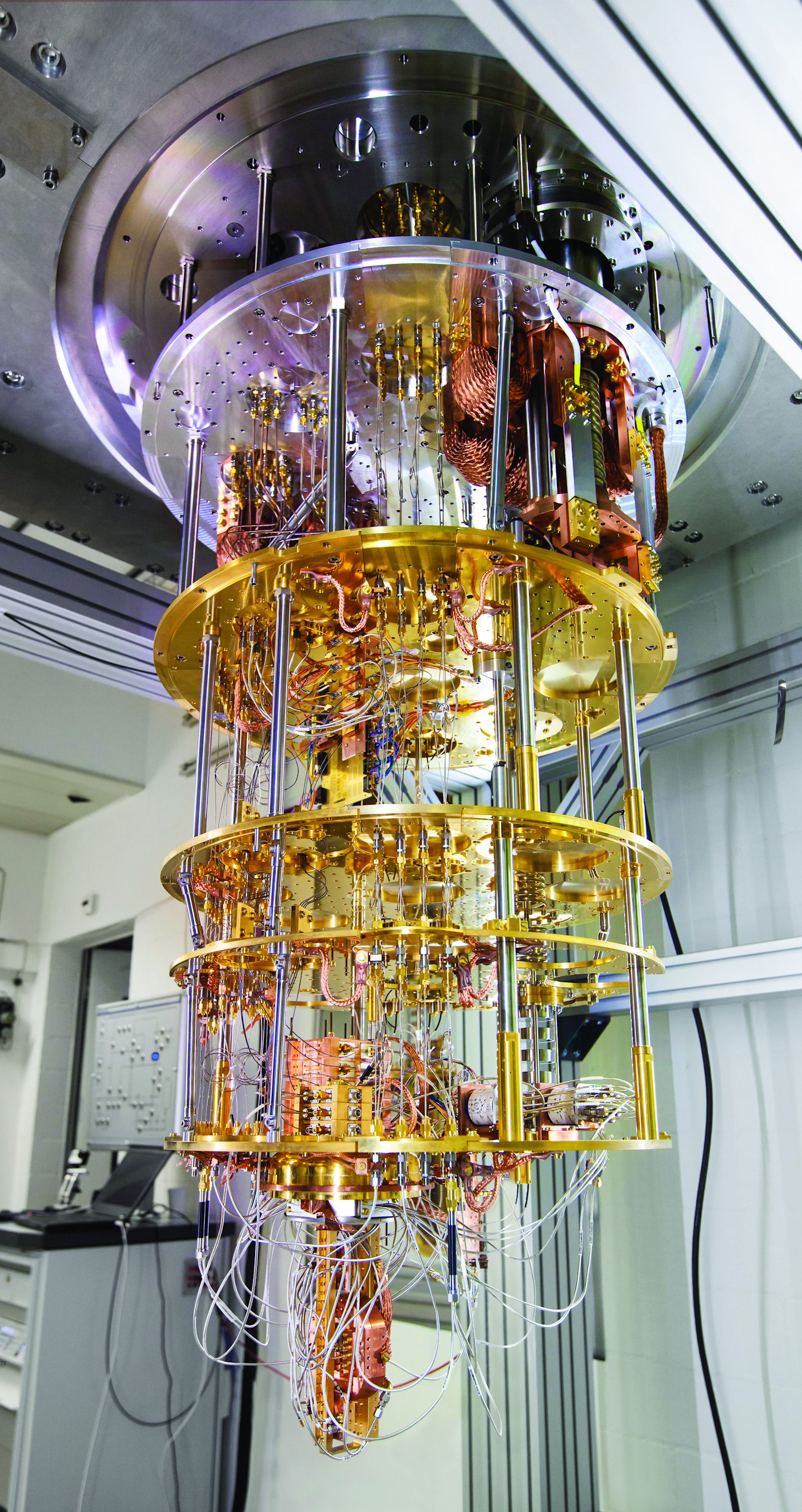 This quantum computer based on superconducting qubits is inserted into a dilution refrigerator and cooled to a temperature less than 1 Kelvin. It was built at IBM Research in Zurich.Although computer researchers have made great strides in AI over the last 30-plus years, this technology still is in its infancy. Systems designers today are nowhere near the armies of intelligent robots of science fiction. Today’s AI relies on innovative computer programming, parallel-processing capabilities of advanced general-purpose graphics processing units (GPGPUs), high-performance embedded computing (HPEC), and similar enabling technologies to create what passes for machine intelligence.
This quantum computer based on superconducting qubits is inserted into a dilution refrigerator and cooled to a temperature less than 1 Kelvin. It was built at IBM Research in Zurich.Although computer researchers have made great strides in AI over the last 30-plus years, this technology still is in its infancy. Systems designers today are nowhere near the armies of intelligent robots of science fiction. Today’s AI relies on innovative computer programming, parallel-processing capabilities of advanced general-purpose graphics processing units (GPGPUs), high-performance embedded computing (HPEC), and similar enabling technologies to create what passes for machine intelligence.
Artificial intelligence can be a tough term to pin down. Is it real intelligence? Probably not. Essentially it describes a computer’s ability to learn from its experience — particularly from its mistakes, like a human does. The aim is to pull relevant data out of experience and then do what a computer does best, which is to process that data very quickly.
That processing speed is key for today’s AI technology. In specific tasks like enabling manned and unmanned aircraft to navigate to and from their mission areas, and making sure the right equipment is on the battlefield to supply the troops, AI can make decisions more quickly than humans can. Results of AI computing also are likely to be more consistent than human decisions, because computers don’t get tired, distracted, or have bad days at the office.
To give an idea of the importance of AI to the warfighter, the U.S. military plans to spend $800 million for AI research in 2021. Among the Pentagon’s leaders in AI research is the Defense Advanced Research Projects Agency (DARPA) in Arlington, Va. DARPA researchers are working on enabling an unmanned jet fighter to dogfight successfully with manned fighters in the AlphaDogfight trials.
DARPA also is pursuing the Ditto: Intelligent Auto-Generation and Composition of Surrogate Models project to develop a new class of computer-generated design models with embedded machine-learning algorithms to help engineers develop and train artificial intelligence (AI) systems more quickly and accurately than they can today. Another recent DARPA AI project is Fast Event-based Neuromorphic Camera and Electronics (FENCE) to enable intelligent electro-optical sensors for tactical military applications.
Not to be outdone, the U.S. Air Force Research Laboratory at Wright-Patterson Air Force Base, Ohio, launched the Soaring Otter program last November to develop fast and efficient ways to move enabling technologies for machine autonomy from the laboratory to flight testing. This project focuses on AI, machine learning, neural networks, neuromorphic computing, and data exploitation.
Quantum computing, meanwhile, is even younger than AI, and seeks to work with quantum bits which can be in many different states at the same time, unlike conventional computing that uses on binary on or off states. Researchers say quantum computers will be able to solve complex problems quickly that no classical computer could solve in any feasible amount of time.
Hypersonic munitions
Think of a cruise missile that can travel at five times the speed of sound, which is faster than 3,600 miles per hour. That’s about one mile per second, and is what military leaders mean when they describe hypersonic munitions. This is a disruptive technology that in a short time has forced top military leaders to reshuffle their research spending plans. Hypersonics represents one of the Pentagon’s highest priorities — so much so that the military plans to spend $3.2 billion for hypersonics research this year.
Why is hypersonic technology so important? Think of a surface warship under threat of hypersonic anti-ship missiles. An opposing ship or aircraft that attacks with hypersonic missiles from 100 miles away will have less than two minutes to react. That means just 100 seconds to detect the incoming threat, classify it, decide on the most effective course of action, and deploy countermeasures. That’s not much time, and it’s a good bet that hypersonic missiles can overwhelm air-defense sensors and countermeasures.
The problem gets a lot worse when and if hypersonic missiles can be developed that are substantially faster than Mach 5. Double that speed, and it cuts  Special Operations cyber warfighters upload coordinates during an exercise showcasing the capabilities of the Advanced Battle Management System. Cyber security is crucial for sensitive battle-management systems.detection, reaction, and defense time in half. Now ask a warship commander if he relishes the notion of less than a minute of warning time of hypersonic missile attack. These are the reasons that U.S. military leaders are considering developing hypersonic munitions and defenses against these weapons as equally important.
Special Operations cyber warfighters upload coordinates during an exercise showcasing the capabilities of the Advanced Battle Management System. Cyber security is crucial for sensitive battle-management systems.detection, reaction, and defense time in half. Now ask a warship commander if he relishes the notion of less than a minute of warning time of hypersonic missile attack. These are the reasons that U.S. military leaders are considering developing hypersonic munitions and defenses against these weapons as equally important.
Such battlefield conditions will require vast advances in computational capabilities, and likely will involve the latest generations of artificial intelligence and quantum computing. Not only that, but hypersonic munitions will require big leaps in rugged electronics for guidance, propulsion systems, sensors, and tactical datalinks. A hypersonic missile must withstand extreme operation conditions akin to a spacecraft re-entering Earth’s atmosphere. Crucial electronic components must be able to operate through heat, shock, and vibration like no weapon’s system ever has.
The nose cones of such missiles will be reinforced against the extreme temperatures of hypersonic flight through the atmosphere, would be immune to direct-energy weapons like high-energy lasers. Counter-hypersonic weapons, instead, must concentrate on the missile’s less-protected body as it passes over defense systems. That would create its own set of challenges. The need to target a hypersonic missile’s vulnerable mid-body would require tracking and targeting at speeds beyond human capability — another application of AI.
On the front lines of hypersonics technology development are The contractors are the Boeing Co. Phantom Works in Washington; the Lockheed Martin Corp. Skunk Works segment in Palmdale, Calif.; and the Raytheon Technologies Corp. Missiles & Defense segment in Tucson, Ariz.
Autonomous unmanned vehicles
Unmanned vehicles operating on land, in the air, and at sea have been around for quite some time. The difference between today’s unmanned vehicles and those of the future, however, is full autonomy. Today’s unmanned vehicles, for the most part, do not operate and make decisions on their own. Instead, most of them are remotely operated, with a human in the loop, and are likely to remain so for the foreseeable future.
What will separate today’s unmanned vehicles and those of the future will be the ability to make independent decisions with little or no human intervention. This will mean planning routes, selecting weapons, compensating for unforeseen circumstances during missions, interacting with other unmanned vehicles, and even for unmanned systems to work closely together in swarms.
There is an understandable reluctance to unleash fully autonomous unmanned vehicles on the battlefield because of the potential for conflict among unmanned An Air Force Cadet uses a Ludwieg tube, a type of wind tunnel, to measure the pressures, temperatures, and flow fields of basic geometric and hypersonic research vehicles. vehicles and human commanders, accountability for decisions on deploying weapons, and the potential for humans to lose strategic control over unmanned forces.
An Air Force Cadet uses a Ludwieg tube, a type of wind tunnel, to measure the pressures, temperatures, and flow fields of basic geometric and hypersonic research vehicles. vehicles and human commanders, accountability for decisions on deploying weapons, and the potential for humans to lose strategic control over unmanned forces.
Nevertheless, enabling technologies like artificial intelligence, quantum computing, and high-performance embedded computing are likely to make autonomous unmanned vehicles too difficult to resist — especially for mundane or dangerous tasks like battlefield resupply, explosives detection and disposal, ocean reconnaissance, and persistent surveillance.
Uncoupling unmanned vehicles from human operators and giving the unmanned systems full autonomy also will be necessary to enable drones to work together on their own as teams or in swarming behavior. Enabling technologies for full machine autonomy in the near term will include fast heterogeneous embedded computing, GPGPUs that offer parallel processing, networked sensors, and advanced computer algorithms. In the far term quantum computing most likely will be applied.
Cyber security and cyber warfare
The ability to keep computers and digital networking free from the prying eyes of hackers, and from all forms of computer malware, is more important today than it ever has been — and the imperative to implement trusted computing measures grows more important with each passing year.
U.S. military organizations are requiring encryption and similar cyber security for most acquisition programs, and defense contractors who handle secret or sensitive digital information must have approved measures in place to monitor suspicious network traffic and block any unauthorized attempts to log on to their networks.
Power grids, water treatment and distribution facilities, hospitals, traffic control, aviation, railroads, sea transport, space-based communications, position, time and navigation – all are part of the cyber domain. That domain also encompasses home appliances, office equipment, children’s toys, medical devices, TV sets, unmanned vehicles, baby monitors, and espionage.
One indicator of the importance of trusted computing and cyber security is the amount that Pentagon officials plan to spend this year: $9.8 billion, which up 81 percent from $5.4 billion requested for 2020.
One year ago U.S. Department of Defense (DOD) leaders were to release new cyber security standards that represented the new cost of doing business in attempts to require universal auditing of contractors’ cyber safeguards. The military’s vast commercial supply chain, especially smaller vendors, has emerged as a critical national security weakness. About 300,000 contractors are to be subject to these standards, which DOD has dubbed the Cybersecurity Maturity Model Certification, or CMMC.
More recently DOD was set to adopt an initial zero-trust architecture by the end of 2020, in an effort to switch from a network-centric to a data-centric modern  A specially modified NC-130H aircraft equipped with the Advanced Tactical Laser weapon system fired its laser while flying over White Sands Missile Range, N.M., successfully hitting a target board located on the ground.information security model. Zero trust means an organization does not inherently trust any user. Trust must be continually assessed and granted in a granular fashion. This allows defense agencies to create policies that provide secure access for users connecting from any device, in any location.
A specially modified NC-130H aircraft equipped with the Advanced Tactical Laser weapon system fired its laser while flying over White Sands Missile Range, N.M., successfully hitting a target board located on the ground.information security model. Zero trust means an organization does not inherently trust any user. Trust must be continually assessed and granted in a granular fashion. This allows defense agencies to create policies that provide secure access for users connecting from any device, in any location.
Last summer the U.S. Air Force Research Laboratory Information Directorate in Rome, N.Y., launched a potential $950 million Agile Cyber Technology 3 (ACT 3) to develop enabling technologies for the U.S. military to achieve cyber superiority.
The ACT 3 program will emphasize enabling technologies for user requirements; prototype technologies for evaluation in an operational environment; and ways for the Air Force to buy limited product quantities necessary for operational introduction. Technical requirements will encompass rapid development, design, prototyping, demonstration, scenario development, experimentation and evaluation, integration, testing, technical installation, initial operations and cyber technologies.
Directed-energy weapons and high-energy lasers
Reliable laser weapons are among today’s most sought-after military capabilities. These weapons operate at the speed of light, and may represent one of the few ways possible for surface warships, military bases, and logistics centers to defend themselves from advanced enemy hypersonic weapons. Supplies of ammunition also is a big advantage; laser weapons never run out of bullets — providing they have an adequate supply of electrical power.
One of the biggest technological challenges to widespread deployment of laser weapons, however, is size, weight, and power consumption (SWaP). These systems tend to be large, heavy, and power-hungry, which prevents them — at least in the near term — from being deployed on tactical jet fighter aircraft, and other relatively small and SWaP-constrained military platforms. Another challenge is scaling-up the output power of laser weapons sufficiently to destroy or disable enemy systems like jet fighters and armored combat vehicles.
This is the reason that today’s most promising laser weapons platforms are Navy surface warships where prototypes already are being deployed to defend these vessels from cruise missiles, manned and unmanned aircraft, swarming fast maneuverable missile boats, and even from modern-day pirates.
As early as 2014 the Navy deployed the AN/SEQ-3 Laser Weapon System (LaWS) from Kratos Defense & Security Solutions in San Diego aboard the amphibious transport dock USS Ponce while the ship operated in and around the Persian Gulf. Most recently the Navy has deployed a counter drone dazzler laser weapon called the Optical Dazzling Interdictor (ODIN) aboard the guided missile destroyer USS Dewey. ODIN is configured to track and disable enemy unmanned aerial vehicles (UAVs) by throwing them off course and jamming their sensors.
Laser weapons are not confined only to large platforms like surface warships, however. The U.S. Marine Corps has tested a portable ground-based laser weapon called the Compact Laser Weapons System (CLaWS) for shooting down enemy UAVs on small combat vehicles like the Humvee or Joint Light Tactical Vehicles (JLTV).
5G wireless communications
Emerging fifth-generation wireless communications — better-known as 5G — for the military holds the promise of ubiquitous high-speed data connectivity: vastly improved intelligence, surveillance, and reconnaissance (ISR); fast and secure command and control; more efficient logistics; swarming unmanned vehicles; and wide use of virtual reality and augmented reality for simulation, training, and mission rehearsal.
The promise of 5G is for instant situational awareness anywhere on Earth, smart hypersonic weapons with re-targeting on-the-fly, rich access to mission-critical data on the leading edge of the battlefield, and unmanned aircraft that can fly safely alongside passenger aircraft in commercial airspace.
 A U.S. Air Force F-22 Raptor and F-35A Lightning II manned combat aircraft fly in formation with the XQ-58A Valkyrie low-cost unmanned aerial vehicle over the U.S. Army Yuma Proving Ground testing range, Ariz.5G, however, will not come easily, quickly, or inexpensively. When compared to the overall 5G vision for the military, commercial interests, and for the consumer, the technology today only is in its infancy — despite the advertising we see on TV from cell phone providers. Bringing the 5G future to fruition will require time, much testing, experimentation, investment — and a whole lot more cell towers than we have today.
A U.S. Air Force F-22 Raptor and F-35A Lightning II manned combat aircraft fly in formation with the XQ-58A Valkyrie low-cost unmanned aerial vehicle over the U.S. Army Yuma Proving Ground testing range, Ariz.5G, however, will not come easily, quickly, or inexpensively. When compared to the overall 5G vision for the military, commercial interests, and for the consumer, the technology today only is in its infancy — despite the advertising we see on TV from cell phone providers. Bringing the 5G future to fruition will require time, much testing, experimentation, investment — and a whole lot more cell towers than we have today.
5G is to increase the speed, reduce the latency, and improve reliability of data transfer compared to existing 4G technologies, and support interconnected or autonomous devices like smart homes, self-driving vehicles, precision agriculture and industrial machinery, and advanced robotics, according to the U.S. Congressional Research Service in Washington, in an October report titled National Security Implications of Fifth Generation (5G) Mobile Technologies.
For the military, 5G could improve ISR systems and signal processing, enable new command-and-control applications, and streamline logistics. 5G also could give the military broad access to augmented and virtual reality, 5G smart warehousing, distributed command and control, and dynamic spectrum use. Military leaders plan to spend $1.5 billion for military microelectronics and 5G networking this year.
The U.S. Department of Defense (DOD) 5G Strategy report, published last May, says 5G has the potential to transform military capabilities. “Ubiquitous high-speed connectivity will also transform the way militaries operate,” according to the report. “Tomorrow’s warfighters will use local and expeditionary 5G networks to move massive amounts of data to connect distant sensors and weapons into a dense, resilient battlefield network.
“This data-rich environment will fuel powerful algorithms that will allow commanders to better understand, shape, and adapt to complex and contested physical and information environments,” the report continues. “Low-latency communications will enable new generations of unmanned and autonomous weapons systems across all domains. The warfighter will be empowered with far richer access to data at the tactical edge, so that even small units can achieve strategic effects.”
Virtual reality in
simulation and training
Military forces do their best to ensure their training is as realistic as possible, and travel to far-flung places like the jungles of Central America, snowy mountains in Alaska, and to deserts of the Southwest to ensure they train in the same conditions in which they are expected to fight.
Now consider: what if warfighters could train in realistic conditions without ever leaving their home bases — sometimes without ever leaving their buildings?
Virtual- and augmented-reality training and mission rehearsal have the potential to save perhaps millions of dollars from the Pentagon’s operations and maintenance budget by enabling warfighters to practice their missions on computer-generated ranges, rather than on distant training centers. Plus, warfighters could train individually or in networked groups virtually any time, without having to wait in line for precious range time.
Virtual reality creates an entire scene, and those using it typically use special headsets on which they view and interact with these simulated environments. Augmented reality, conversely, generates only part of the scene when viewed through battlefield goggles or night-vision devices. It’s a computer-assisted heads-up display for infantry warfighters.
Among the enabling technologies of virtual- and augmented reality are general-purpose graphics processing units (GPGPUs), electro-optical headsets, wearable electronics, smart phones and tablet computers, and sometimes devices like treadmills that enable users to run, jump, and roll to enhance realism.
Open systems and SOSA
Open-systems standards for embedded computing and other kind of military electronics are being devised for rapid technology insertion, rapid technology development, and to promote industry competition by enabling many third-party component suppliers to participate in large military projects. If they can build to an open standard, chances are good they can provide embedded computing technology without running afoul of proprietary systems.
One of the highest-profile open-systems standards taking shape today is the Sensor Open Systems Architecture (SOSA), which seeks to drive down the cost and complexity of aerospace and defense electronics components and systems by adopting and then enforcing the use of widely accepted open-systems standards to promote component interoperability; rapid technology insertion and upgrades; reuse; and critical mass in the supplier market.
SOSA is going through its last pre-releases called snapshots, and then SOSA 1.0 should roll out early this year. SOSA has support from the U.S. Army, Navy, and Air Force, as well as from a broad range of embedded computing suppliers in industry.
 AT&T technicians and civilian contractors assemble a “Cell on Wings” drone to provide 5G connectivity for the Advanced Battle Management Systems Onramp 2 at White Sands Missile Range, N.M.SOSA seeks to take the best of several influential industry standards, such as OpenVPX; the Tri-Service Memo mentions the Future Airborne Capability Environment (FACE); Hardware Open Systems Technologies (HOST); Vehicular Integration for C4ISR/EW Interoperability (VICTORY); Open Mission Systems/Universal Command and Control Interface (OMS/UCI); Command, Control, Communications, Computers, Intelligence, surveillance and Reconnaissance (C4ISR) / Electronic Warfare (EW) Modular Open Suite of Standards (CMOSS); and Modular Open RF Architecture (MORA).
AT&T technicians and civilian contractors assemble a “Cell on Wings” drone to provide 5G connectivity for the Advanced Battle Management Systems Onramp 2 at White Sands Missile Range, N.M.SOSA seeks to take the best of several influential industry standards, such as OpenVPX; the Tri-Service Memo mentions the Future Airborne Capability Environment (FACE); Hardware Open Systems Technologies (HOST); Vehicular Integration for C4ISR/EW Interoperability (VICTORY); Open Mission Systems/Universal Command and Control Interface (OMS/UCI); Command, Control, Communications, Computers, Intelligence, surveillance and Reconnaissance (C4ISR) / Electronic Warfare (EW) Modular Open Suite of Standards (CMOSS); and Modular Open RF Architecture (MORA).
The idea is to form industry consensus on standards that already have momentum in the embedded systems market, as well as to adopt the core of other standards into SOSA. That way it’s not a far leap for systems designers that meet the guidelines of FACE, VICTORY, OMS/UCI, CMOSS, or MORA to conform to SOSA.
Moreover, SOSA seeks to narrow down OpenVPX standards to a manageable level that is appealing to the Pentagon. For example, SOSA reduces OpenVPX slot profiles from 37 to three; 3U switch profiles from 24 to three; and 6U slot profiles from 19 to three, Littlefield points out.
SOSA also seeks to settle on 12-volt power to make it less likely that systems designers will need custom-designed power conditioning and control, as well as offer certified solutions for software packages such as security and system management.




More Stories
From Novice to Expert: Your Software Developer Journey
Software Developer: Navigating a Thriving Career
How to Stand Out as a Software Developer