[ad_1]
A pay-for every-install (PPI) malware services recognised as PrivateLoader has been spotted distributing a “fairly innovative” framework referred to as NetDooka, granting attackers total command about the contaminated units.
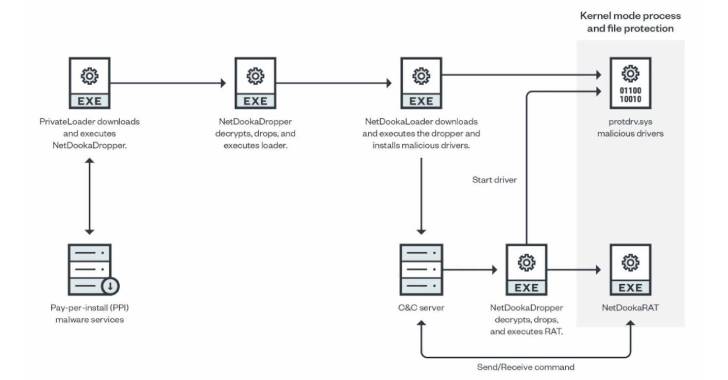
“The framework is dispersed by means of a shell out-per-put in (PPI) services and is made up of several areas, together with a loader, a dropper, a protection driver, and a comprehensive-featured distant entry trojan (RAT) that implements its own community communication protocol,” Craze Micro mentioned in a report printed Thursday.
PrivateLoader, as documented by Intel 471 in February 2022, capabilities as a downloader liable for downloading and installing added malware onto the contaminated program, such as SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.
Showcasing anti-assessment techniques, PrivateLoader is created in the C++ programming language and is stated to be in active progress, with the downloader malware family members getting traction between many danger actors.
PrivateLoader bacterial infections are typically propagated by means of pirated software program downloaded from rogue websites that are pushed to the major of research outcomes by using lookup motor optimization (Search engine optimization) poisoning methods.
“PrivateLoader is at present made use of to distribute ransomware, stealer, banker, and other commodity malware,” Zscaler famous past 7 days. “The loader will very likely proceed to be updated with new capabilities and performance to evade detection and effectively provide 2nd-stage malware payloads.”
The framework, even now in its enhancement period, incorporates different modules: a dropper, a loader, a kernel-method course of action and file safety driver, and a distant accessibility trojan that works by using a custom protocol to talk with the command-and-control (C2) server.
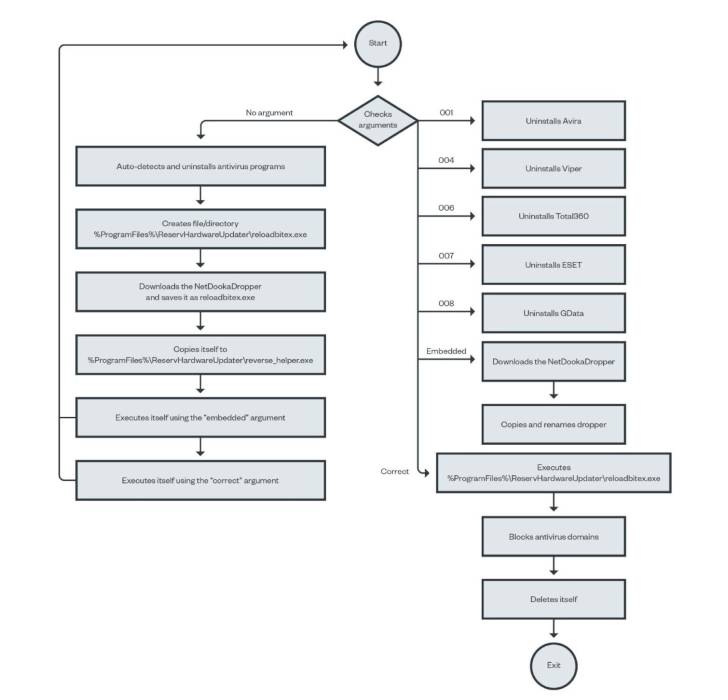
The freshly noticed set of bacterial infections involving the NetDooka framework commences with PrivateLoader performing as a conduit to deploy a dropper ingredient, which then decrypts and executes a loader that, in turn, retrieves another dropper from a distant server to set up a comprehensive-highlighted trojan as properly as a kernel driver.
“The driver part functions as a kernel-degree safety for the RAT element,” scientists Aliakbar Zahravi and Leandro Froes reported. “It does this by attempting to avoid the file deletion and process termination of the RAT element.”
The backdoor, dubbed NetDookaRAT, is noteworthy for its breadth of performance, enabling it to operate instructions on the target’s system, carry out distributed denial-of-assistance (DDoS) assaults, obtain and send out data files, log keystrokes, and download and execute supplemental payloads.
This signifies that NetDooka’s abilities not only enable it to act as an entry issue for other malware, but can also be weaponized to steal delicate info and sort distant-controlled botnets.
“PPI malware products and services allow malware creators to simply deploy their payloads,” Zahravi and Froes concluded.
“The use of a destructive driver creates a large assault floor for attackers to exploit, while also letting them to take advantage of methods these types of as protecting procedures and data files, bypassing antivirus systems, and hiding the malware or its community communications from the program.”
[ad_2]
Resource url




More Stories
SEO Service: From Keywords to Conversions
How SEO Service Boosts Website Traffic and Visibility
Essential Elements of a Winning SEO Service