
Getty Visuals
Substantial-performance computer networks, some belonging to the world’s most notable corporations, are below assault by a recently found backdoor that gives hackers the ability to remotely execute instructions of their choice, researchers reported on Tuesday.
Kobalos, as researchers from safety organization Eset have named the malware, is a backdoor that runs on Linux, FreeBSD, and Solaris, and code artifacts advise it may perhaps have the moment run on AIX and the ancient Home windows 3.11 and Home windows 95 platforms. The backdoor was produced into the wild no later on than 2019, and the team driving it was energetic throughout very last calendar year.
Multistriped backdoor
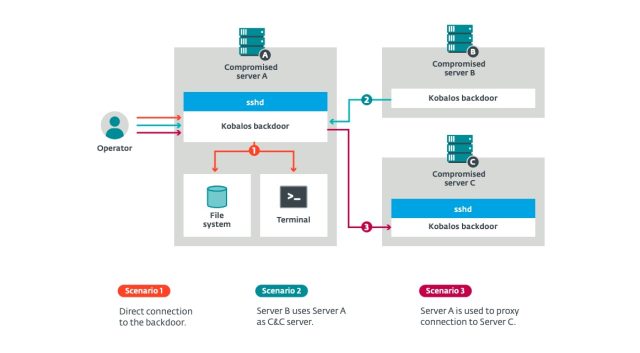
Though the Kobalos style and design is advanced, its functionalities are limited and almost fully relevant to covert backdoor accessibility. As soon as entirely deployed, the malware presents entry to the file system of the compromised technique and enables accessibility to a remote terminal that offers the attackers the capacity to operate arbitrary instructions.
In just one manner, the malware acts as a passive implant that opens a TCP port on an infected device and waits for an incoming relationship from an attacker. A independent mode allows the malware to transform servers into command-and-control servers that other Kobalos-contaminated equipment connect to.
Infected devices can also be used as proxies that link to other servers compromised with Kobalos. These proxies can be chained so that the operators can use numerous Kobalos-compromised devices to arrive at their remaining targets.
The determine beneath exhibits an overview of the Kobalos functions:
Eset
To retain stealth, Kobalos encrypts communications with contaminated devices employing two 16-byte keys that are created and then encrypted with a password-guarded RSA-512 private essential. All inbound and outbound traffic from then on is RC4-encrypted working with the two keys. The malware employs a complex obfuscation mechanism that makes third-occasion evaluation challenging.
Compact amount of elite targets
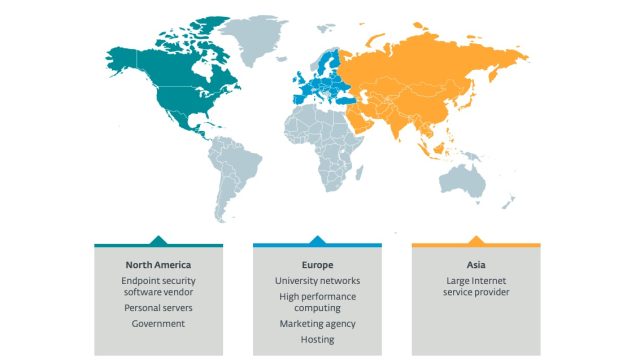
Individuals infected with the malware incorporate a university, an close-issue security business, authorities companies, and a substantial ISP, between many others. A single large-general performance laptop or computer compromised had no less than 512 gigabytes of RAM and just about a petabyte of storage.
Eset mentioned the quantity of victims was calculated in the tens. The variety will come from an Online scan that measures habits that occurs when a link is proven with a compromised host from a unique source port. The impression below shows that the victims were being found in the United States, Europe, and Asia:
Eset
The robustness of the malware, mixed with the tiny range of popular targets, demonstrates that Kobalos is the get the job done of an advanced team of hackers, particularly in the a lot less-traveled path of non-Windows-primarily based malware.
“The several nicely-carried out functions and the community evasion tactics present the attackers driving Kobalos are a great deal more professional than the regular malware author focusing on Linux and other non-Windows systems,” Eset researchers Marc-Etienne M.Léveillé and Ignacio Sanmillan wrote in a report. “Their targets, remaining really high-profile, also exhibit that the objective of the Kobalos operators is not to compromise as several programs as feasible. Its small footprint and community evasion techniques may well describe why it went undetected till we approached victims with the success of our Net-vast scan.”
So much, it is not apparent how Kobalos is acquiring put in. A ingredient that steals credentials that administrators utilized to log in to devices employing the SSH protocol is one chance, but it’s not likely it is really the sole implies of infection. It can be also unclear specifically what the Kobalos operators are undertaking with the malware. There were no signs that compromised methods have been applied to mine cryptocurrency or carry out other compute-intense tasks.
“The intent of the authors of this malware is still unknown,” they wrote. “We have not discovered any clues to point out regardless of whether they steal confidential information, pursue financial attain, or are after a little something else.”




More Stories
How News Technology is Shaping Public Opinion
Exploring Ethics in News Technology Practices
News Technology: Enhancing Audience Engagement