Companies in the monetary solutions sector are large-benefit targets for cybercriminals. In modern several years, extra innovative botnets and other bad bot attack strategies have enabled malicious hackers to ratchet up the velocity of attacks on this sector. The 4 most common techniques hackers deploy botnets is for credit history card fraud, account takeover (ATO) assaults, distributed denial of services (DDoS) assaults, and scraping content from economic solutions web sites. Every single of these assault strategies success in quite particular consequences for the influenced group.
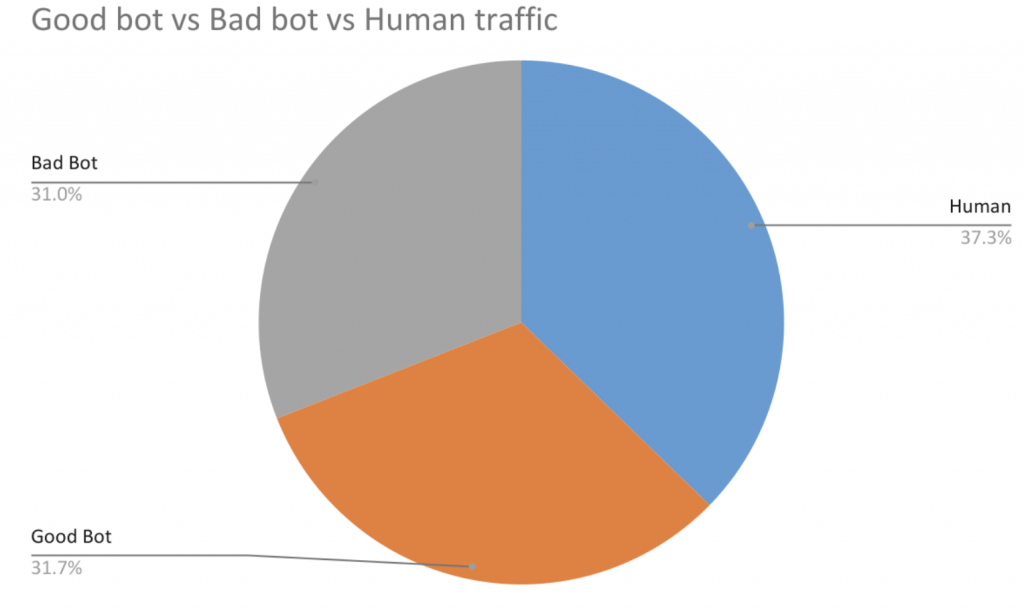
The Imperva Negative Bot Report 2021 lists economical services among the the prime five industries focused by advanced lousy bot visitors. Lousy bots are software program applications that run automatic responsibilities with destructive intent over the net and the worst bots undertake felony functions, these types of as fraud and outright theft. They permit large-speed abuse, misuse, and assaults on your internet websites, mobile apps, and APIs. Bots that carefully mimic human habits and are more durable to detect and stop. Because the beginning of 2021, only 37% of monetary services web page targeted traffic is human and all over just one-third (31%) of all targeted visitors to fiscal services web pages has been built up of lousy bots.
In this publish, we will consider a nearer seem at 4 negative bot assault techniques that today’s cybercriminals usually use against monetary providers companies. We’ll also give you some suggestions about how to stop negative bots from negatively impacting your firm.
Credit rating card fraud
What is it
The undesirable bot-leveraging credit score card fraud procedure most normally made use of by hackers is card cracking. Cracking is dependent on the idea that it is effortless to acquire a credit score card variety, recognised as a Private Account Quantity (PAN), jointly with the title printed on the card. Attackers use bots to guess and verify the additional facts necessary to “crack” and illicitly use a credit history card. There are several means criminals can receive PANs: Getting lists of PANs on the darkish web, as a result of accomplices doing work in retail or restaurants who are exposed to credit history card information and facts, incorporating a gadget to a credit card swiper that enables unauthorized events to read the card facts and PIN (also acknowledged as skimming), and by phishing cons, which commonly entail contacting the credit rating card operator and pretending to be an approved social gathering requesting their credit rating card particulars.
In a massive-scale procedure, the standard attackers’ method is:
- Obtain a record of PANs.
- Set up a bot that can attempt tiny buys on a big record of payment web sites. The bot must endeavor a buy on a web site, publishing credit score card details for a PAN, and just about every time guessing a diverse mixture of CVV, expiration and postal code.
- Deploy the bot to function on 30 payment websites in parallel, to avoid guessing boundaries.
This technique would allow for an attacker to crack a card each 4 seconds, and scale up the course of action to crack as numerous as 21,600 stolen credit score playing cards for every day.
How to stop it
Device fingerprinting
Fingerprinting brings together the user’s browser and system to realize who or what is connecting to the assistance. Poor bots attempting credit rating card fraud will have to make various attempts, and can’t adjust their unit just about every time. They ought to swap browsers, apparent their cache, use personal or incognito mode, use digital machines or unit emulators, or use highly developed fraud resources like FraudFox or MultiLogin. Machine fingerprinting can help detect browser and product parameters that continue to be the exact amongst periods, indicating the exact same entity is connecting yet again and once again. Fingerprinting technologies can produce a one of a kind machine, browser and cookie identifier, which, if shared by multiple logins, raises a suspicion that all individuals logins are portion of a fraud try.
Browser validation
Some malicious bots pretend to run a distinct browser, and then cycle via user agents to avoid staying detected. Browser validation makes sure each and every consumer browser is what it claims to be – that it has the expected JavaScript agent, is making phone calls in a way to be expected from that browser, and is functioning in a way that is envisioned from human end users.
Machine mastering conduct examination
Serious users visiting payment websites show normal habits styles. Bots will typically behave very otherwise from this sample, but in techniques you simply cannot often outline or detect in advance. You can use behavioral evaluation technology to evaluate person actions and detect anomalies – users or particular transactions that are anomalous or suspicious. This can enable discover undesirable bots and avoid cracking attempts. As portion of behavioral investigation, try out to examine as significantly information as possible, together with URLs accessed, website engagement metrics, mouse actions, and cellular swipe conduct.
Track record analysis
There are quite a few known computer software bots with predictable technological and behavioral styles or originating IPs. Having accessibility to a database of recognised bot designs can aid you recognize bots accessing your internet site. Website traffic that may perhaps seem at very first glance to be a genuine person can be quickly recognized by cross-referencing it with identified fingerprints of poor bots.
Progressive challenges
When your techniques suspect a consumer is a bot, you really should have a progressive system for “challenging” the person to examination if they are a bot or not. Progressive tests indicates that you try the the very least intrusive technique to start with, to limit disruption to real buyers. Below are various issues you can use:
Cookie problem – transparent to a genuine person
JavaScript obstacle – slightly slows down user experience
CAPTCHA – most intrusive
Other actions to bolster your stability perimeter towards cracking bots include things like:
Multi-aspect authentication
eCommerce web pages can involve customers to indication in with a little something they know (for example, a password) and some thing they have (for example, a cellular cellular phone). Even though this does not prevent cracking, it makes it more difficult for criminals to create significant numbers of faux accounts, and renders it virtually extremely hard for them to get more than current accounts.
API protection
eCommerce internet sites typically use credit card APIs, these types of as these offered by PayPal or Square, to facilitate transactions. These APIs can be susceptible to assaults, this kind of as JavaScript injection or the rerouting of information, if not incorporated with the appropriate security. To safeguard versus many of these attacks, eCommerce web-sites can use a blend of Transportation Layer Stability (TLS) encryption and robust authentication and authorization mechanisms, like all those made available by OAuth and OpenID.
Account takeover (ATO) attacks
What is it
ATO assaults a.k.a. credential stuffing is a method in which attackers use lists of compromised user qualifications to breach a technique. The assault utilizes bots for automation and scale and is based mostly on the assumption that numerous persons reuse usernames and passwords across numerous services. Figures display that about .1% of breached qualifications tried on another company will result in a prosperous login. Credential stuffing is a climbing risk vector for two main explanations:
- Wide availability of massive databases of breach credentials, for instance, “Selection #1-5” which manufactured 22 billion username and password mixtures openly obtainable in simple text to the hacker neighborhood.
- Far more advanced bots that at the same time attempt numerous logins, and show up to originate from various IP addresses. These bots can generally circumvent basic protection actions like banning IP addresses with way too a lot of unsuccessful logins.
In a substantial-scale credential stuffing exploit, the attacker:
- Sets up a bot that is equipped to instantly log into a number of consumer accounts in parallel, even though faking distinctive IP addresses.
- Runs an automated system to verify if stolen credentials work on many sites. Functioning the course of action in parallel across numerous web-sites reduces the want to regularly log into a one assistance.
- Displays for prosperous logins and obtains personally identifiable information and facts, credit playing cards or other beneficial knowledge from the compromised accounts.
- Retains account information and facts for long run use, for example, phishing assaults or other transactions enabled by the compromised services.
How to avoid it
In addition to system fingerprinting, multi-element authentication, and CAPTCHA you can use:
IP Blacklisting
Attackers will generally have a minimal pool of IP addresses, so an additional productive defense is to block or sandbox IPs that attempt to log into many accounts. You can monitor the very last a number of IPs that were being made use of to log into a specific account and review them to the suspected poor IP, to cut down fake positives.
Rate-Restrict Non-Residential Targeted visitors Resources
It is easy to discover targeted visitors originating from Amazon Web Expert services or other business data centers. This site visitors is virtually unquestionably bot website traffic and really should be dealt with a great deal more very carefully than standard person visitors. Use strict amount restrictions and block or ban IPs with suspicious conduct.
Block Headless Browsers
Headless browsers these kinds of as PhantomJS can be simply determined by the JavaScript calls they use. Block accessibility to headless browsers simply because they are not genuine customers, and just about surely point out suspicious habits.
Disallow E mail Addresses as Consumer IDs
Credential stuffing depends on the reuse of the similar usernames or account IDs throughout services. This is significantly additional possible to come about if the ID is an e mail handle. By avoiding people from making use of their e mail address as an account ID, you dramatically reduce the opportunity of them reusing the exact same user/password pair on an additional website.
Dispersed denial of company (DDoS) assaults
What is it
Hackers frequently deploy a botnet, a group of hijacked online-linked gadgets, every single injected with malware used to control it from a remote locale without the need of the know-how of the device’s rightful proprietor to carry out DDoS attacks. Layer 7 (software layer) DDoS assaults target the top rated layer or the application layer of the OSI model which will help facilitate connections around web protocol. The aim is to overwhelm server sources by flooding a server with so significantly site visitors in the sort of requests to hook up until eventually it is no for a longer time able of responding. The better the amount of requests for each next (RPS) the far more extreme the assault.
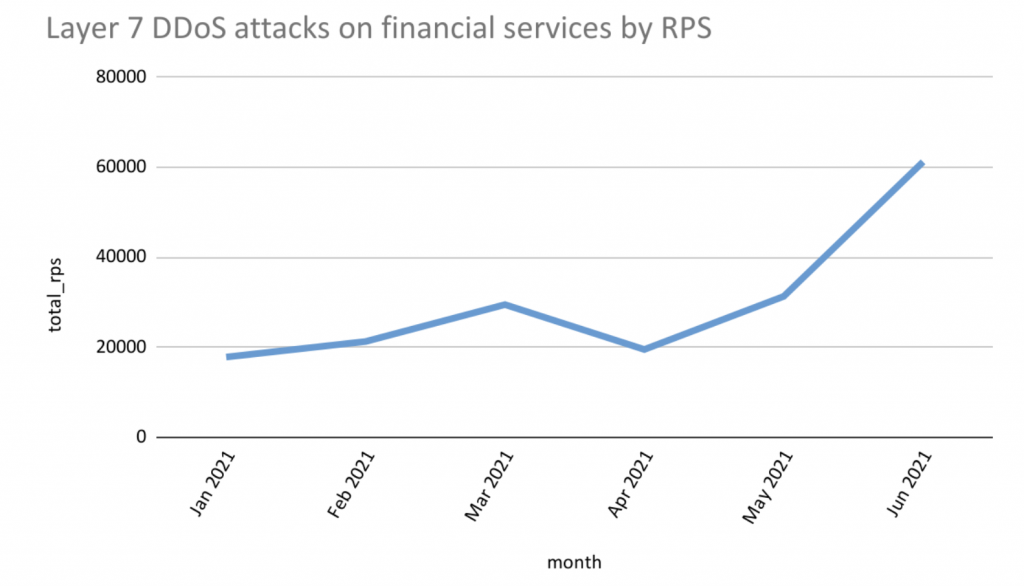
Data monitored by Imperva Investigate Labs reveals the range of requests for each next (RPS) in Layer 7 DDoS attacks against economic expert services targets has noticeably elevated given that April 2021. This is in line with the CTI risk score which also reveals a surge in the danger possibility from April.
How to prevent it
Imperva supplies straightforward to use, cost-effective and thorough DDoS safety that pushes the envelope for cloud-based mostly mitigation technologies.
By a blend of on-desire and normally-on options, a world wide network that delivers around-limitless scalability and filtering answers for transparent mitigation, Imperva fully safeguards clients from DDoS attacks.
Articles scraping
What is it
World wide web scraping is the method of employing bots to extract articles and knowledge from your internet site. Contrary to display scraping, which only copies pixels shown on-display, internet scraping extracts fundamental HTML code and, with it, facts stored in a databases. The scraper can then replicate entire web site content material elsewhere. This is an concern for financial expert services corporations simply because when hackers steal your written content (e.g. released personal loan curiosity rates, product added benefits, etcetera.) they are a parasite on your efforts. Copy information damages your Website positioning rankings. Explain to-tale indications of written content scraping are unexplained web-site slowdowns and downtime can be triggered by aggressive scrapers.
There are several important variances to enable distinguish in between legit and destructive articles scraping bots. Reputable bots are identified with the firm for which they scrape. For illustration, Googlebot identifies by itself in its HTTP header as belonging to Google.
Malicious bots, conversely, impersonate genuine website traffic by creating a wrong HTTP consumer agent.
Reputable bots obey a site’s robot.txt file, which lists these pages a bot is permitted to access and individuals it cannot. On the other hand, destructive scrapers crawl the website irrespective of what the website operator has allowed.
How to prevent it
To counter innovations manufactured by malicious bot operators, Imperva utilizes granular site visitors evaluation. It ensures that all visitors coming to your web-site, human and bot alike, is totally legit. The approach consists of the cross verification of aspects, which include:
HTML fingerprint
The filtering approach starts off with a granular inspection of HTML headers. These can present clues as to irrespective of whether a visitor is a human or bot, and malicious or protected. Header signatures are as opposed versus a frequently up to date database of around 10 million recognized variants.
IP name
Imperva collects IP knowledge from all attacks versus our shoppers. Visits from IP addresses owning a record of staying utilised in assaults are addressed with suspicion and are extra likely to be scrutinized further.
Behavior assessment
Tracking the means readers interact with a internet site can expose irregular behavioral styles, such as a suspiciously aggressive charge of requests and illogical searching designs. This allows identify bots that pose as human guests.
Progressive troubles
Imperva uses a set of problems, such as cookie help and JavaScript execution, to filter out bots and limit bogus positives. As a very last vacation resort, a CAPTCHA challenge can weed out bots making an attempt to pass themselves off as humans.
The submit The 4 most prevalent poor bot attack strategies focusing on money services appeared initial on Blog.
*** This is a Protection Bloggers Network syndicated site from Blog site authored by Bruce Lynch. Read the initial put up at: https://www.imperva.com/weblog/the-4-most-frequent-undesirable-bot-attack-procedures-focusing on-economical-expert services/




More Stories
SEO Service: From Keywords to Conversions
How SEO Service Boosts Website Traffic and Visibility
Essential Elements of a Winning SEO Service